By John Patzakis
X1’s recent webinar announcing the availability of true “AI in-place” for the enterprise was both highly attended and strongly validated by the audience response. The session did more than introduce a new feature; it articulated a fundamentally different architectural approach to enterprise AI—one designed explicitly for security, compliance, and scalability in complex, distributed environments. Our central message was simple: enterprise AI adoption has been constrained not by lack of interest, but by architectural and security requirements that existing platforms have failed to address.
That reality was most powerfully captured in a quote shared on the opening slide from a Fortune 100 Chief Information Security Officer, which set the tone for the entire discussion:
“Normally AI for infosec and compliance use cases is a non-starter for security reasons, but your workflow and architecture is completely different. This allows us – all behind our firewall — to develop our own models that are trained on our own data and customized to our specific security and compliance use cases and deployed in-place across our enterprise.”
This endorsement crystallized the webinar’s core insight: AI becomes viable for the most sensitive enterprise use cases only when it is deployed where the data already lives, rather than forcing data into external or centralized systems.
The technical foundation that makes this possible is X1’s micro-indexing architecture. Unlike traditional platforms built on centralized, resource-intensive indexing technologies, X1 deploys lightweight, distributed micro-indexes directly at the data source. This allows enterprises to index, search, and now apply AI analysis without mass data movement. As emphasized during the webinar, centralized indexing is not just expensive and slow—it is fundamentally misaligned with how modern enterprise data is distributed across file systems, endpoints, cloud platforms, and collaboration tools.
The session then highlighted how this architectural distinction resolves a long-standing problem in discovery, compliance, and security workflows. Legacy platforms require organizations to collect and centralize data before they can analyze it, introducing delays, high costs, and significant risk exposure. X1 reverses that workflow. By enabling visibility and AI-driven classification before collection, organizations can make informed, targeted decisions—collecting only what is necessary, remediating issues in-place, and dramatically reducing both risk and operational overhead.
The discussion also demystified large language models (LLMs), explaining that while model training is compute-intensive, models themselves are increasingly commoditized and portable. Critically, LLMs require extracted text and metadata— processed from native files—to function. This aligns perfectly with X1’s existing capability, as text and metadata extraction are already integral to our micro-indexing process. AI models can therefore be deployed alongside these indexes, operating in parallel across thousands of data sources with massive scalability.
The conversation then connected this architecture to concrete, high-value use cases. In eDiscovery, AI in-place enables faster early case assessment and proportionality by analyzing data where it resides. In incident response and breach investigations, security teams can immediately scope exposure across distributed systems without waiting months for data exports. For compliance and governance, AI models can continuously identify sensitive data, enforce retention policies, and surface risk conditions that were previously impractical to monitor at scale.
In addition to a live product demo showcasing this new capability, we concluded the webinar with several clarifying points and announcements. First, we emphasized that X1 does not access, monetize, or host customer data. Also, AI in-place is not an experimental add-on but an enhancement to a proven, production-grade platform. And notably, there is no additional licensing cost for the AI capability itself—customers simply deploy models within their own environment. With proof-of-concept testing beginning shortly and production deployments targeted for April 2026, the webinar made clear that AI in-place is not a future vision, but an imminent reality for the enterprise.
You can access a recording of the webinar here, and to learn more about X1 Enterprise, please visit us at X1.com.


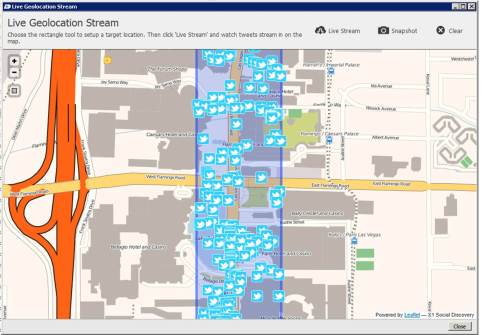
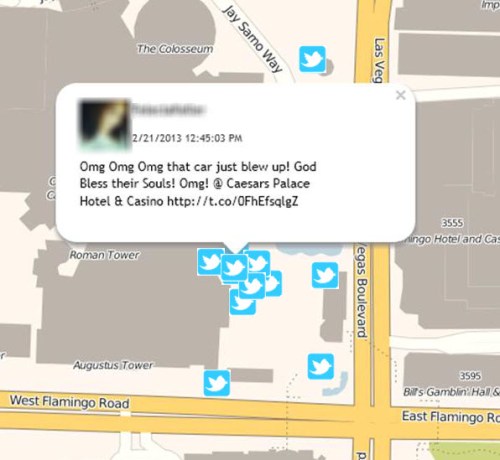
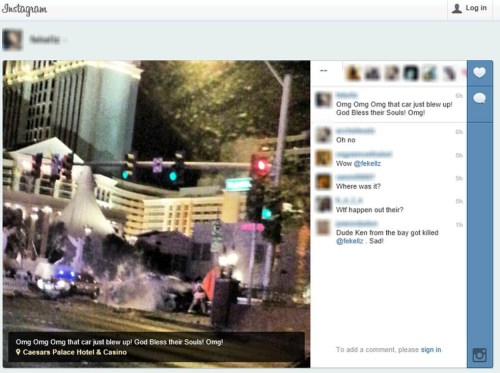



 “leveraging Facebook is just one of many ways law enforcement officials are gleaning evidence from social media to help them solve crimes.” According to a recent survey performed by LexisNexis on federal, state and local law enforcement officials who use social media, 4 of 5 used social media to gather evidence during investigations. Kelly states, “Half said they checked social media at least once a week, and the majority said social media helps them solve crimes faster.”
“leveraging Facebook is just one of many ways law enforcement officials are gleaning evidence from social media to help them solve crimes.” According to a recent survey performed by LexisNexis on federal, state and local law enforcement officials who use social media, 4 of 5 used social media to gather evidence during investigations. Kelly states, “Half said they checked social media at least once a week, and the majority said social media helps them solve crimes faster.”
